Building a Strong Incident Response Strategy: Practical Steps for Better Cybersecurity
Cyber incidents are inevitable — preparation separates disruption from recovery. This guide walks you through practical steps to build an incident response plan that helps your organization detect threats faster, reduce downtime, and protect sensitive data. We cover the core phases of response, frameworks that fit small and mid-sized businesses, who should be on your response team, and why Northern Utah businesses benefit from a locally tailored approach.
Key steps in an incident response plan
An incident response plan gives your team a clear, repeatable path for handling cybersecurity events. It’s a roadmap that helps you move from discovery to full recovery while preserving evidence and reducing business impact.
The six phases of incident response
- Preparation: Build and train your response team, document policies, and ensure tools and backups are in place.
- Detection and analysis: Monitor systems, verify alerts, and assess the scope and severity of potential incidents.
- Containment: Isolate affected systems and stop the incident from spreading while preserving data for investigation.
- Eradication: Remove malware, close exploited paths, and patch systems so the threat can’t return.
- Recovery: Bring systems back online in a controlled way, validate integrity, and resume normal operations.
- Post-incident activity: Conduct a lessons-learned review, update the plan, and strengthen defenses based on findings.
Working through these phases gives you a structured, repeatable process to manage incidents from start to finish.
How each phase supports incident management
Preparation reduces response time. Detection catches issues before they escalate. Containment limits damage. Eradication removes the root cause. Recovery restores services safely. Post-incident reviews turn experience into improvements. Together, these phases improve resilience and reduce overall risk.
Which frameworks work best for SMBs?
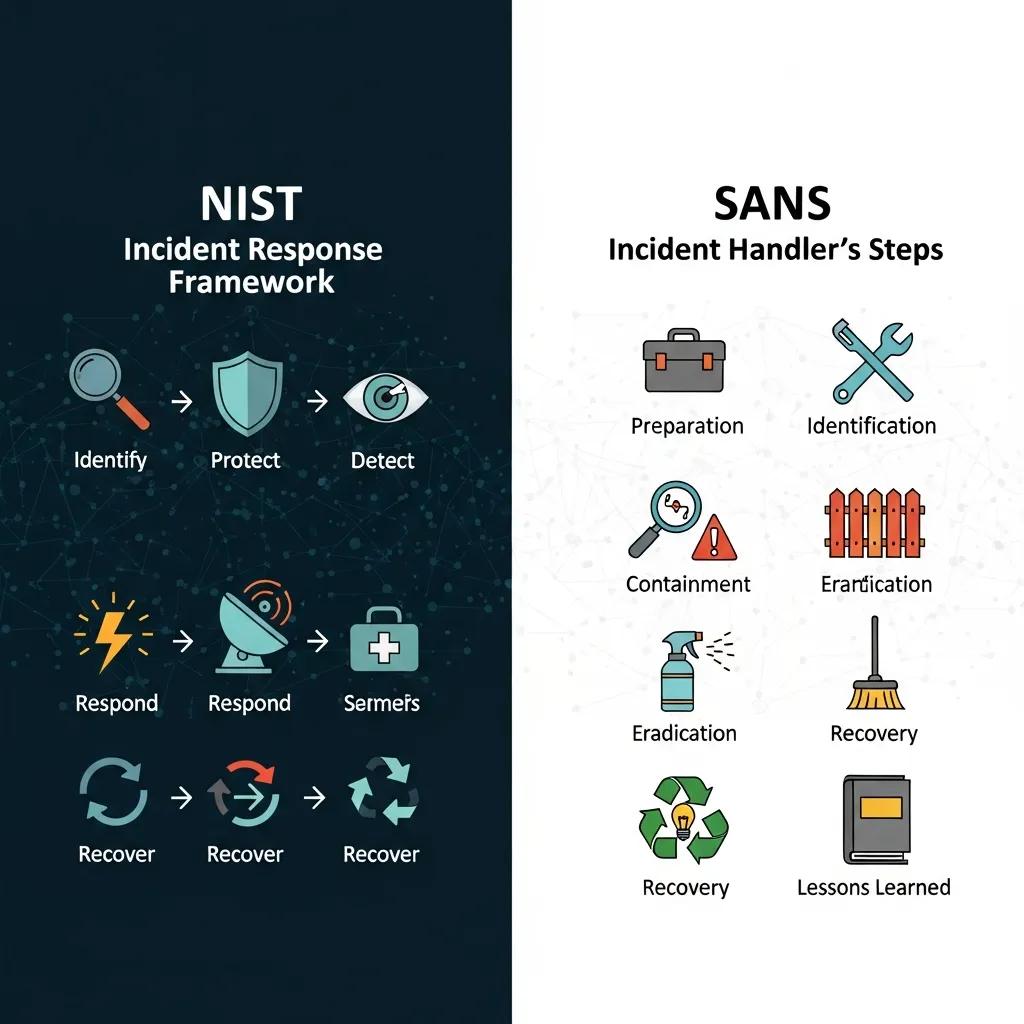
Smaller organizations benefit from clear, practical frameworks that scale to their resources. Two widely used approaches are the NIST Incident Response Lifecycle and the SANS Incident Response Framework — both give a reliable structure you can adapt to fit your team and budget.
About the NIST Incident Response Framework
NIST lays out a six-step lifecycle that’s easy to follow and map to your existing processes. It’s a solid starting point for SMBs that want a standards-based, repeatable approach to incident handling and recovery.
How the SANS framework compares
SANS covers many of the same phases but focuses more on operational playbooks and response checklists. That makes it useful if you want straightforward, action-oriented steps your IT staff can follow during an event. Choose the framework that best matches your team’s size and operational style.
Who should be on your incident response team?
Your response team should bring together the right mix of technical, operational, and legal skills so decisions can be made quickly and correctly.
Key roles and responsibilities

- Incident Response Manager: Leads the response, coordinates stakeholders, and makes go/no-go decisions.
- Security Analyst: Investigates alerts, traces the attack path, and recommends technical containment steps.
- IT Support: Executes system isolation, restores backups, and handles system rebuilds.
- Legal Advisor: Guides compliance, breach notifications, and communications to regulators and customers.
Each role speeds recovery and ensures decisions are balanced across technical, business, and legal needs.
Why coordination matters
Clear responsibilities and regular practice make responses faster and less error-prone. Use tabletop exercises and simulations so the team knows who does what under pressure — that familiarity saves time when it counts.
Research shows incident response teams are often assembled to match the situation — ad hoc and flexible rather than fixed.
Incident Response Team Functionality & Ad Hoc Formation
We studied the nature of incident response teams in seven Operations Centers of varying size and types including service providers, a Security Operations Center, a Data Center, and two military training Operations Centers. All responded to incidents by forming teams. We asked: what is the context of incident response work? how can we model incident response work? Today’s incident response team is ad hoc, i.e., tailor-made to the circumstances, and responsive to changing circumstances.
Incident response teams in IT operations centers: the T-TOCs model of team functionality, S Greenspan, 2016
How Northern Utah businesses gain from a tailored incident response plan
Local businesses do best with plans that reflect their systems, vendors, and response times. Partnering with our regional experts means your plan fits your operations, rather than forcing a one-size-fits-all solution. Work with our Ogden IT team to build a plan that works for your business and community.
Advantages of personalized cybersecurity support
- Local expertise: Providers familiar with the area can recommend practical controls and trusted vendors.
- Proactive defense: Customized measures target your specific vulnerabilities before they become incidents.
- Faster response: Local support reduces downtime with quicker on-site or remote assistance.
These benefits make a tailored incident response strategy a smart investment for local organizations.
How Crossaction Business IT Solutions supports incident response
Crossaction Business IT Solutions provides focused IT and cybersecurity services for Northern Utah businesses. We offer malware and virus protection, secure email configurations, and layered hardware and network defenses. By combining proactive monitoring with local, rapid support, Crossaction helps you detect issues sooner and recover faster when incidents occur.
| Phase | Description | Key Activities |
|---|---|---|
| Preparation | Establish readiness | Training, policy development |
| Detection | Identify incidents | Monitoring, analysis |
| Containment | Limit impact | Isolation, access control |
| Eradication | Remove threats | Malware removal, patching |
| Recovery | Restore operations | System restoration, testing |
| Post-Incident | Review and improve | Analysis, updates to plan |
This table summarizes the phases and typical activities to help you build a clear, operational incident response plan.
Frequently Asked Questions
What challenges do organizations face when rolling out an incident response strategy?
Common obstacles include limited staff or budget, insufficient hands-on training, and keeping up with evolving threats. Many teams also struggle to integrate response plans into day-to-day workflows. Overcome these by prioritizing core controls, scheduling regular drills, and reviewing the plan after real incidents.
How often should we test and update our incident response plan?
Test at least once a year and after any major change (new systems, staff changes, or a real incident). Quarterly tabletop exercises or focused drills help keep roles sharp; follow each test with a review and plan updates.
What role does communication play in incident response?
Clear, pre-defined communication channels and templates prevent confusion. Fast internal communication keeps the team aligned, while coordinated external messages protect customers and regulators. Define who speaks for the organization and what they can say.
How can we measure the effectiveness of our incident response efforts?
Track metrics like time to detect, time to contain, time to recover, and the number of repeat incidents. Post-incident reviews, audit findings, and tabletop outcomes also reveal where to improve.
What legal issues should businesses consider during incident response?
Legal obligations may include breach notification laws, data protection requirements, and contractual obligations. A legal advisor should be part of your plan to guide reporting timelines, evidence handling, and communications to regulators and affected parties.
How do we keep our incident response team well trained?
Maintain a training program with regular workshops, tabletop exercises, and hands-on drills. Encourage certifications and vendor training, and rotate roles during exercises so multiple people can step in when needed.

