Small Business Cybersecurity: Myths, Facts, and Practical Steps to Protect Your Company
Today’s digital environment puts small businesses at risk in ways many owners don’t expect. This article clears up common cybersecurity myths, explains who’s targeted, shows the limits of antivirus, clarifies cloud responsibilities, and outlines affordable protections so you can make smarter security decisions.
Are Small Businesses Really Targets for Cyberattacks? Debunking the Myth
It’s a mistake to think attackers only go after big firms. Small businesses are attractive because they often have fewer safeguards and easier access.
What Evidence Shows Small Businesses Are Frequent Cyberattack Victims?
About 43% of attacks affect small businesses, and many breached firms close within months. Breaches cause financial loss, reputation damage, and legal exposure.
How Does Being a Target Impact Small Business Security Strategies?
Accepting you’re a target shifts priorities: budgeting, staff training, regular reviews, and stronger tools. Treat cybersecurity as a core business function for lasting protection.
Is Antivirus Software Enough? Understanding Layered Security for Small Businesses
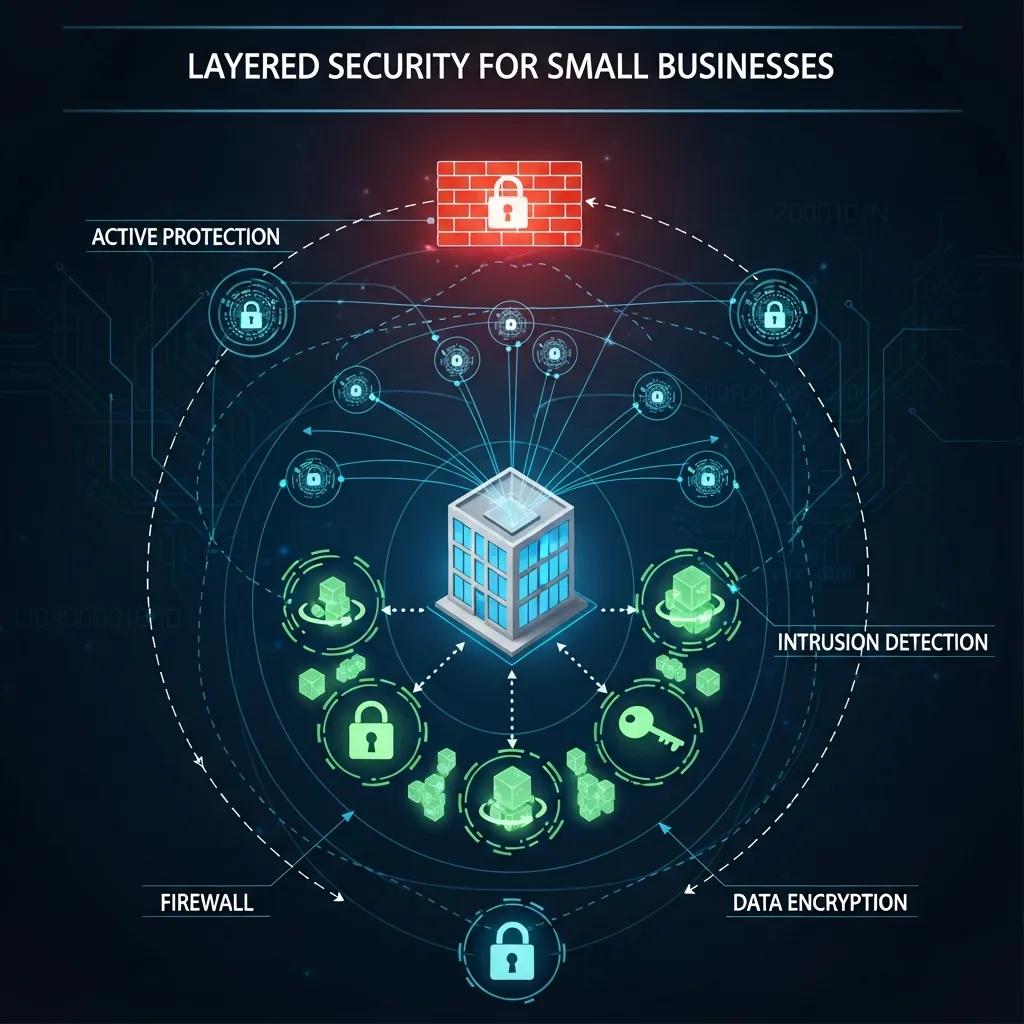
Antivirus is a necessary first layer but won’t stop phishing, ransomware, or novel exploits. A layered security strategy reduces overall risk.
Why Is Antivirus Insufficient Alone for Comprehensive Cybersecurity?
Signature-based antivirus can miss new or targeted threats like zero-days and sophisticated phishing. Use antivirus alongside other defenses rather than as the sole control.
What Are the Key Components of a Layered Security Approach?
Combine tools and practices so gaps in one area are covered by others. Core elements include:
- Firewalls: Control traffic between trusted and untrusted networks to block obvious threats.
- Intrusion Detection Systems (IDS): Monitor network activity and alert you to suspicious behavior so you can act quickly.
- Data Encryption: Keep sensitive information unreadable to anyone without the proper keys, whether data is stored or moving across networks.
- Regular Software Updates: Apply patches and updates promptly to reduce the window of opportunity for attackers.
Together these elements create a resilient defense that reduces exposure.
Is Cloud Storage Inherently Secure? Clarifying the Shared Responsibility Model
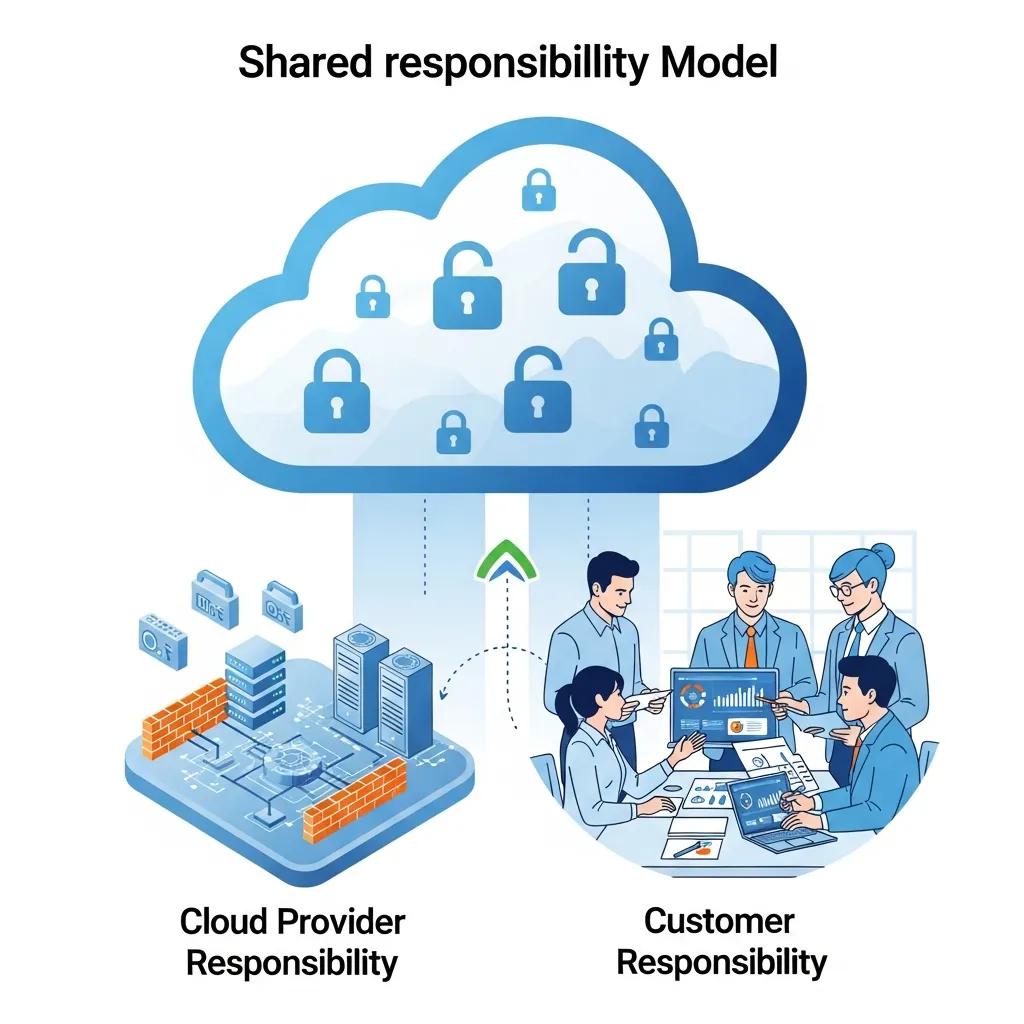
Cloud providers secure infrastructure, but customers must configure access, encryption, and monitoring. The shared responsibility model means you retain key duties.
What Are Common Misconceptions About Cloud Security for Small Businesses?
Don’t assume the provider handles everything. Misconfiguration, weak access controls, and missing encryption leave data exposed.
How Can Small Businesses Effectively Secure Their Cloud Data?
Practical steps:
- Data Encryption: Encrypt data in transit and at rest.
- Access Control: Apply the principle of least privilege and enforce strong authentication.
- Regular Audits: Review cloud settings and permissions on a schedule to catch risky configurations.
Following these practices closes common gaps and reduces risk from misconfiguration.
How Can Small Businesses Afford Cybersecurity? Evaluating Costs vs. Risks
Cybersecurity can feel expensive, but breaches often cost far more. Comparing breach costs to practical investments clarifies ROI.
What Is the True Cost of Cyberattacks Compared to Cybersecurity Investments?
A breach can cost roughly $200,000 in recovery, legal fees, and lost revenue. Preventive measures—policies, training, and managed services—usually cost far less and lower the chance of a costly incident.
What Affordable Cybersecurity Solutions Are Available for Small Businesses?
Affordable, effective options include:
- Managed Security Services: Outsource monitoring and response to get expertise without a large hire.
- Cybersecurity Training: Teach staff to spot phishing and risky behaviors; human awareness is a strong defense.
- Free Cybersecurity Assessments: Use vendor or nonprofit scans to find priorities and quick fixes.
Research consistently shows that training and awareness significantly reduce breach risk for small and medium-sized enterprises.
SME Cybersecurity Training Gaps & Breach Risks
Research finds that large organizations regularly deliver cybersecurity training to prepare staff for threats. Many small and medium-sized enterprises (SMEs), however, lack either the awareness or the budget for consistent training. That gap makes SMEs more vulnerable to breaches, which can harm reputation, expose private data, and impact future business relationships.
Together, these measures help small businesses strengthen their cybersecurity without overspending, especially for businesses in Northern Utah seeking trusted local expertise like Crossaction.
| Cybersecurity Solution | Description | Estimated Cost |
|---|---|---|
| Managed Security Services | Outsourced monitoring and incident response from security specialists | Varies by provider |
| Cybersecurity Training | Structured employee education on phishing, passwords, and safe handling of data | $500 – $2,000 annually |
| Free Cybersecurity Assessments | Initial evaluation to identify weaknesses and quick wins | Free |
The table shows budget-friendly options that let small businesses take concrete steps to protect operations.
Local Cybersecurity Expertise for Northern Utah Businesses
For businesses in Northern Utah, finding reliable local support for cybersecurity and IT needs is crucial. Crossaction provides comprehensive IT support and cybersecurity solutions, helping companies navigate the complexities of digital protection with expert guidance and tailored services. Learn more about their commitment to local businesses and their expertise by visiting Crossaction’s About Us page.
Frequently Asked Questions
What are the most common types of cyberattacks targeting small businesses?
Phishing, ransomware, and denial-of-service (DoS) attacks are the most common. Each targets different weaknesses—employee behavior, critical data, or availability—so prioritize defenses accordingly.
How can small businesses train employees on cybersecurity best practices?
Use short workshops, online courses, and regular refreshers focused on spotting phishing, using strong passwords, and handling sensitive data safely.
What role does incident response play in small business cybersecurity?
A clear incident response plan lets you identify, contain, remove, and restore quickly. Having a plan reduces downtime, cost, and uncertainty during an incident.
Are there specific regulations small businesses need to comply with regarding cybersecurity?
Requirements depend on industry and location; examples include GDPR or HIPAA. Compliance usually means documented controls, regular audits, and careful data handling.
How can small businesses assess their cybersecurity posture?
Run vulnerability scans and penetration tests, use free configuration tools, and consider a security professional for deeper assessment and remediation steps.
What are the benefits of investing in cybersecurity insurance for small businesses?
Cyber insurance can help cover breach-related costs and support recovery, but it complements—does not replace—sound security practices.

